2024_Hgame_week1_re
ezASM
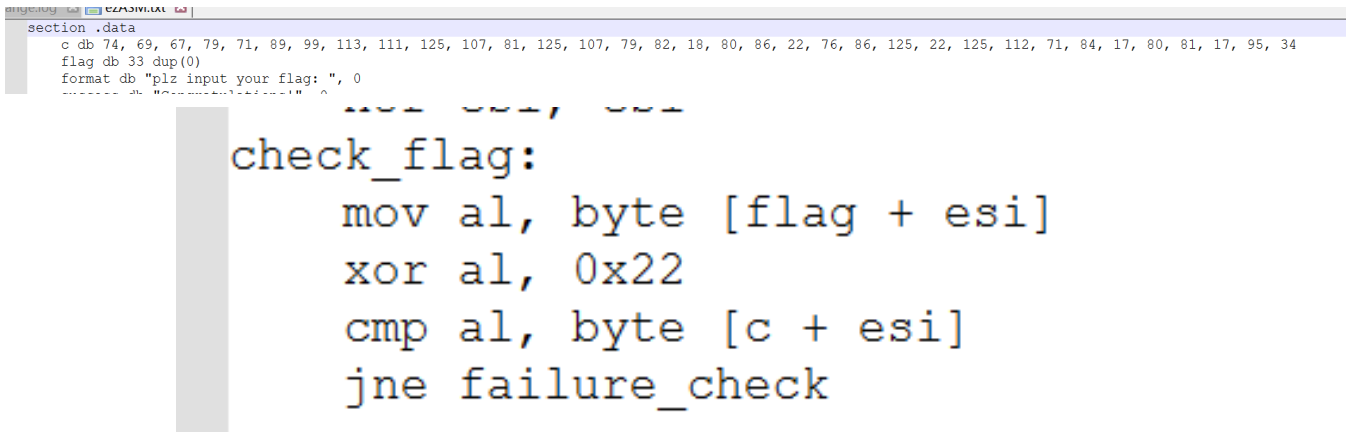
由图可以看出进行了flag和 0x22 的异或
于是写脚本进行逆向
- 运行得到flag
1 | |
1 | |
ezUPX
- 首先把upx壳给去掉
1 | |
- 然后打开IDA查看
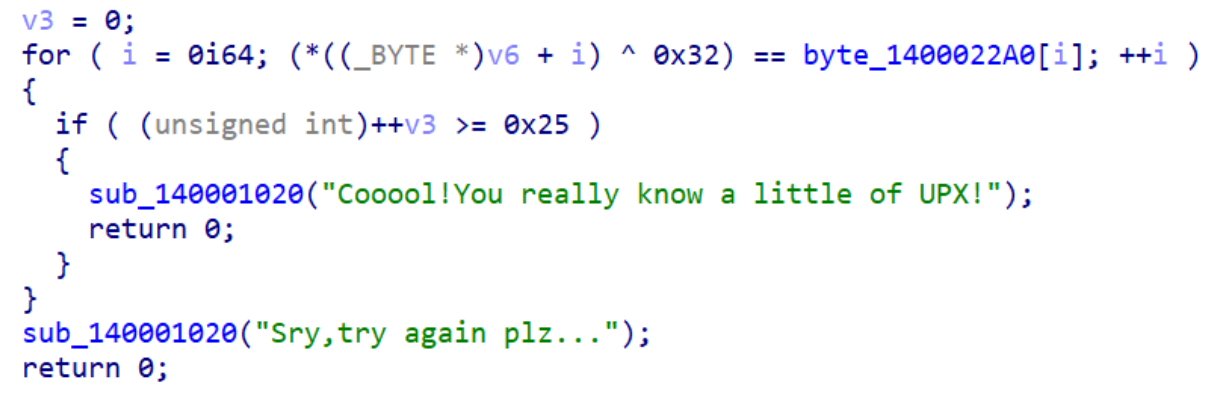
- 能看到一个很明显的加密函数,只需要对这串数字进行异或就能解出答案
- 写一个脚本
1 | |
- 运行就能得到答案
1 | |
2024_Hgame_week1_re
http://example.com/2024/04/14/2024-Hgame-week1-re/

由图可以看出进行了flag和 0x22 的异或
于是写脚本进行逆向
1 | |
1 | |
1 | |

1 | |
1 | |